whitepaper
Detecting Supply Chain Attacks With Deception
Inside You’ll Find
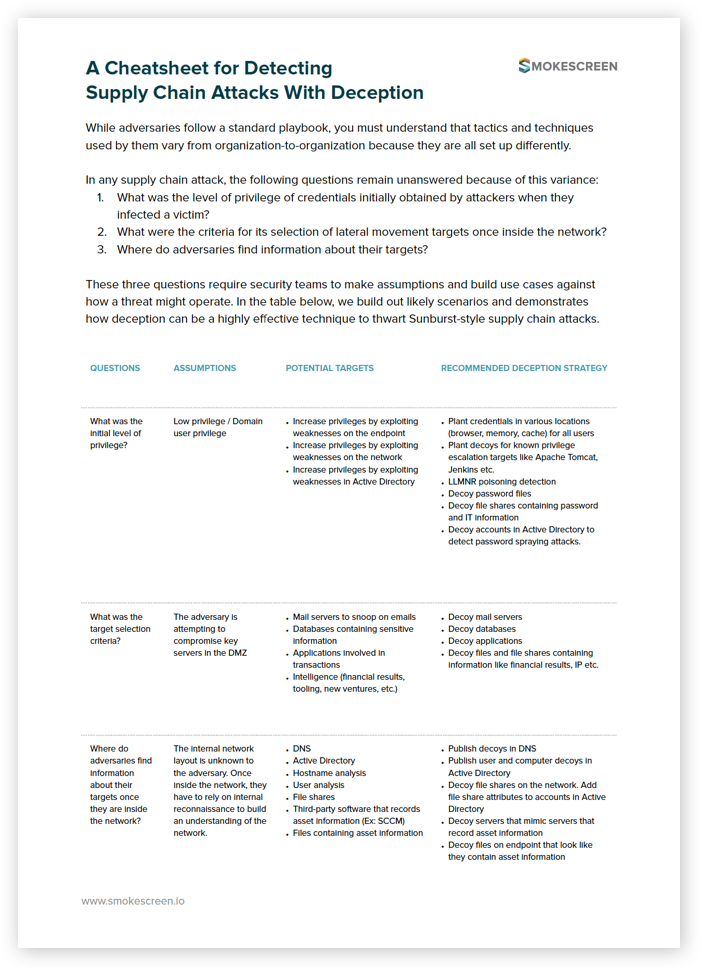
A reference guide for making assumptions and building a deception-based defense strategy to thwart supply chain attacks.
- Three questions that go unanswered in a supply chain attack and can inform your ability to defend against it.
- The different assumptions you can make based on these questions to build out a defense plan.
- The potential targets that attackers go after in a typical supply chain attack.
- Our recommended deception strategy for detecting adversaries that target your network in a supply chain attack.