whitepaper
Detecting Sunburst With Smokescreen
Inside You’ll Find
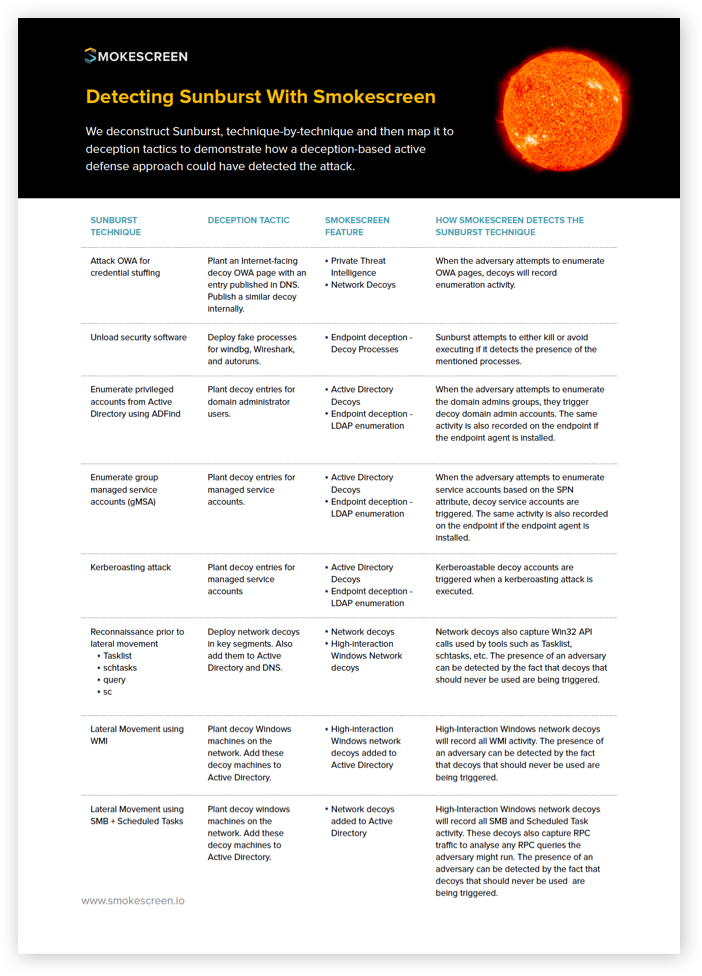
A technique-by-technique deconstruction of the Sunburst attack mapped to deception tactics can detect the techniques.
- Perimeter and network decoys that detect credential stuffing attacks on OWA pages.
- Active Directory and endpoint decoys that detect enumeration of privileged accounts, managed service accounts, and kerberoasting.
- Network and high-interaction Windows decoys that detect reconnaissance prior to lateral movement.
- Network and high-interaction Windows decoys in the Active Directory that detect lateral movement using WMI and SMB.